Introduction:
Single Sign-On (SSO) is an authentication technique where the user uses one set of login credentials to access multiple web applications.About Platform:
. Asp.net core MVC. Microsoft Identity Login
. Dotnet core 2.2
. SQL LocalDB
Core Concept:
In the dotnet core, by sharing authentication cookie we can achieve SSO for the subdomains.A subdomain is a domain which part of another domain. Additional name prefixed to a domain that URL can be a subdomain. For example "http://testmyapp.com/" is a domain, its subdomain looks like "http://mobile.testmyapp.com".
Create MVC Application & LocalDB Setup To IIS & IIS Hosting:
Create an Asp.net MVC Core application by selecting a login individual user template from a visual studio. For this application use, LocalDB as a database then host this application to local IIS, bind "http://testmyapp.com" as domain and "http://mobile.testmyapp.com" as a domain to test sharing authentication cookie.
For hosting Asp.net Core application to localhost and binding domains click here for step by step process. While using LocalDB in IIS any issues click here to fix them.
Test Application Hosting In IIS:
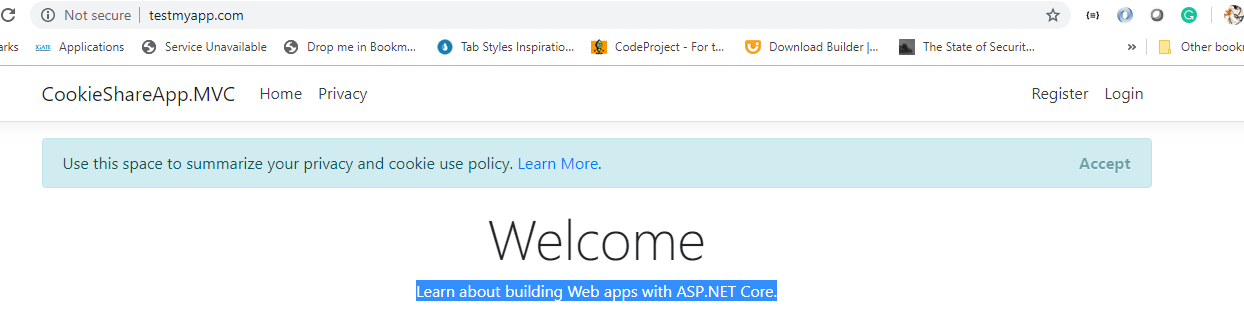
After hosting the application successfully, navigate to the application using "http://testmyapp.com".Here application uses Microsoft Asp.net Identity login by default. Now to test register and get logged in.
Now try to navigate the application using "http://mobile.testmyapp.com" subdomain where you can see the home page as above.
Register Data Protection API Service:
Now open a startup.cs file and in "ConfigureServie()" method we need to register Data Protection API service as below services.AddDataProtection()
.PersistKeysToFileSystem(GetKyRingDirectoryInfo())
.SetApplicationName("SharedCookieApp");
. AddDataProtection().PersistKeysToFileSystem(GetKyRingDirectoryInfo()) here we created self Data Protection key and stored in specific folder.
. "SharedCookieApp" application name where it to be common.
Dynamically Create Data Protection API Key:
Now we need to provide DirectoryInfo to save the Data Protection API key. To do that add the following piece of code as follows private DirectoryInfo GetKyRingDirectoryInfo()
{
string applicationBasePath = System.AppContext.BaseDirectory;
DirectoryInfo directoryInof = new DirectoryInfo(applicationBasePath);
string keyRingPath = Configuration.GetSection("AppKeys").GetValue("keyRingPath");
do
{
directoryInof = directoryInof.Parent;
DirectoryInfo keyRingDirectoryInfo = new DirectoryInfo($"{directoryInof.FullName}{keyRingPath}");
if (keyRingDirectoryInfo.Exists)
{
return keyRingDirectoryInfo;
}
}
while (directoryInof.Parent != null);
throw new Exception($"key ring path not found");
}
here I'm checking the folder path until able to found the path. You can directly assign the physical path, instead of checking for folder path by leveling up a parent folder on every iteration until its found.
Configure Cookie Settings:
Now we need to register cookie configuration to share login cookie between domain and subdomainsas below
services.ConfigureApplicationCookie(options =>
{
options.Cookie.Name = ".AspNet.SharedCookie";
options.Cookie.Domain = ".testmyapp.com";
});
. Cookie.Name login cookie name
. Cookie.Domain to register main domain, so that cookie gets shared to subdomains
Data Protection API Key Path:
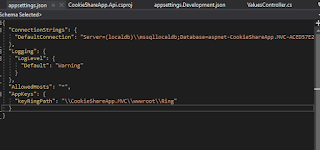
Now add a new folder in wwwroot folder and name it as "Ring". Where Data Protection Key gets created and saved. This key will be used to validate cookies as well as used in the encryption of sensitive data in the cookie.Add the keyring folder path in the appSetting.json file as below
Test Login Cookie Sharing:
Now navigate to "http://testmyapp.com" and get logged in as belowNow navigate to "http://mobile.testmy.com" subdomain and we can observe we are automatically logged in as below
By observing both images, we successfully logged a user in both domain and subdomain using SSO cookie sharing.
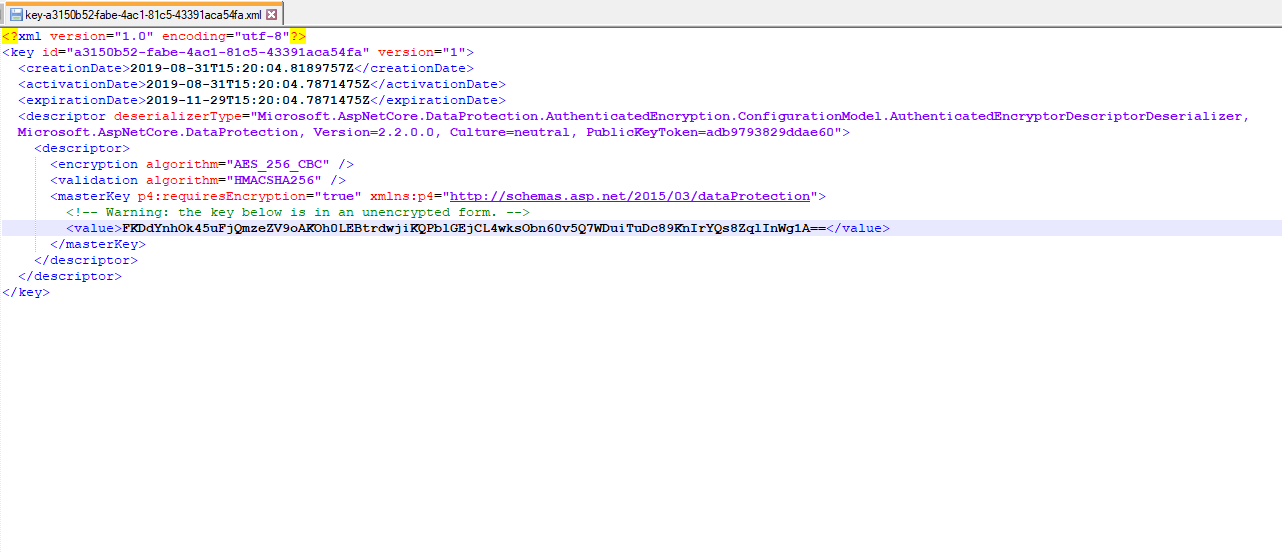
Go to a "Ring" folder physical location used in our application. we can find the Data Protection key will get created which used to encrypting and validating our login cookie. Key sample as below
Summary:
SSO (Single Sign-On) was implemented successfully with subdomains of an application. Cookie encryption and decryption were done with the help of the Data Protection API provided by ASP.NET core. A similar cookie sharing concept can be used for an application runs under another application in IIS click here.
Refer:
. Source Code click here. Part 2: Share Authentication Cookie - Application Runs Under Another Application
. Step by step IIS hosting in Dotnet Core click here
. To fix issues on LocalDB while using IIS click here



Part 2 link is not working
ReplyDeleteI found it https://www.learmoreseekmore.com/2019/09/part-2-share-authentication-cookie.html
DeleteThanks
Deletelink updated
Nice article, but how can I achieve a SSO if you want to share the Authentication from .NET core cookie to ASP.NET 4.6.
ReplyDeleteThank you in advance.
Platform
ASP.NET Core 3.1 --> ASP.NET MVC 4.6